Why select Ancoris as your Google Workspace Premier Partner
Ancoris is only one of a handful of European Google Cloud partners with the Work Transformation Enterprise specialisation. Our deployment experts will help you make a smooth transition―for the technology and for the people using it.
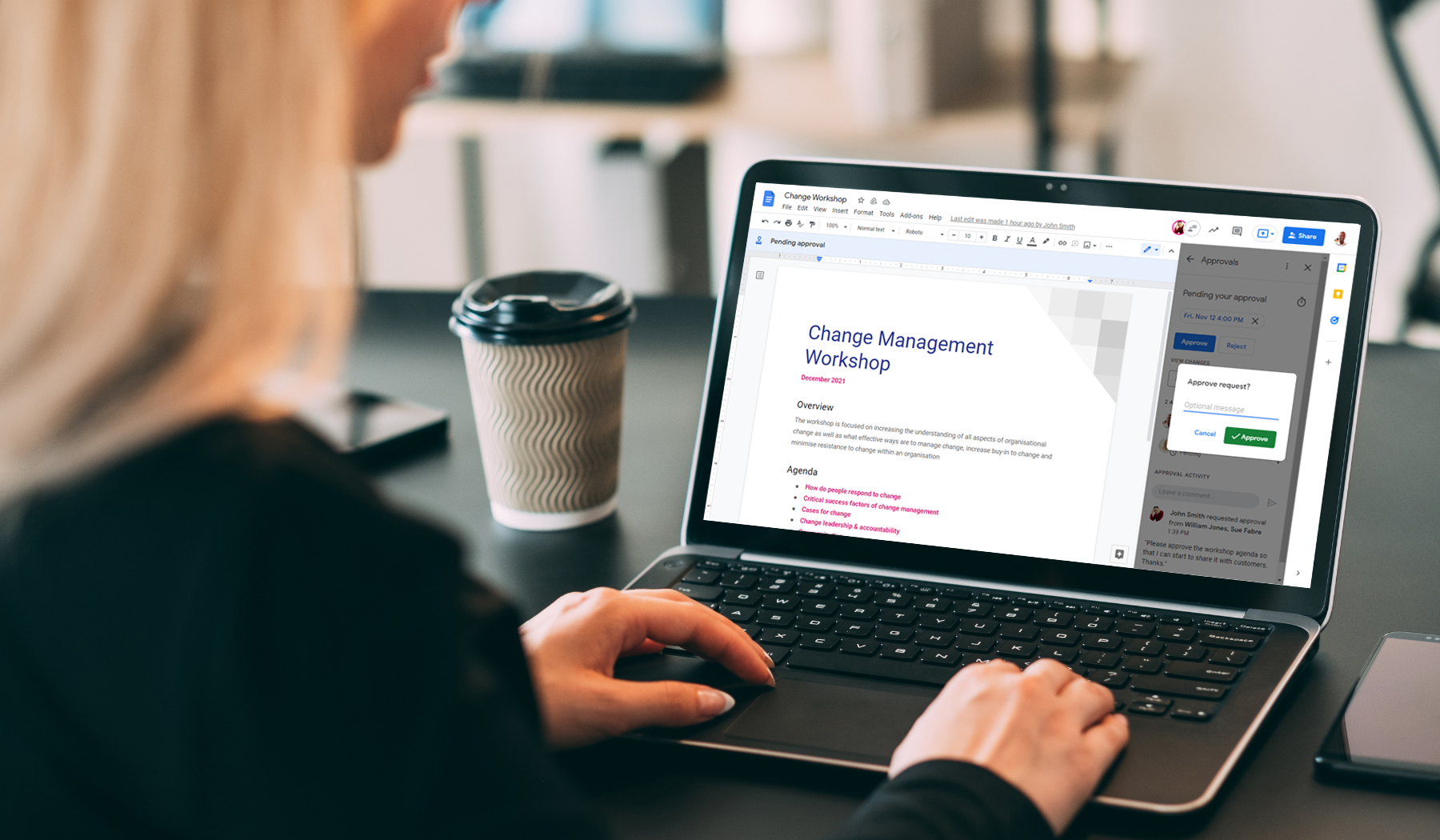
To complement our technical service delivery consultants, we have a dedicated in-house change management and user enablement team to guide you through the process.
Your Going Google intranet, using our Cloud Skills Academy, will provide your end users support after the go live.